2024 Cybersecurity and Cyber Liability Predictions
I’m dusting off my crystal ball to peak a bit into the future for today’s article. I’ve been seeing a lot of optimism about 2024. And, personally, I can’t wait! It’s shaping up to be an incredible year filled with great potential.
On the Cybersecurity and Cyber Liability front though, I’m not so sure that I have the same optimism. 2023 was filled with a lot of advancement in technology and a lot of progress from businesses to adopt and implement better ways of protecting themselves.
My fear is that this could snap back a bit. I suppose it just depends on how well we learned last year and whether we got comfortable after finally catching up to the bare minimums that others and I have been insisting businesses take seriously (for years now).
This will be the year to see how well we’ve learned to be more proactive. Maybe I’ve been around too many skeptical cybersecurity professionals, but I suspect there’s still more we need to figure out this year.
MFA will be imperative in 2024
Businesses have been doing a great job in 2023 implementing MFA. Much of that has been thanks to Cyber Liability, laws, and business-to-business engagements where it’s become a requirement.
However, there’s still a large amount of people not using it. Frankly, they’re probably already compromised and just don’t know it.
There are also others out there using MFA that just isn’t up to par or more easily bypassed in attacks. Not all MFA is equal.
In 2024, we need to continue to make progress on this. Those that don’t have MFA need to put in some work to get it in place. Those that do have it need to make sure it’s done effectively and harden their defenses.
This year, I believe we’ll see attackers respond to this in a couple of ways – looking at more advanced attacks to bypass MFA and looking for other types of attacks beyond authentication.
Bypassing MFA is absolutely possible. This is something I’ll be digging into deeper very soon this year. So, it’s going to be important to layer security tools that can help detect suspicious activity, and that account privileges are tightened to reduce impacts of credential-based compromises.
Exploits will increase as an initial attack vector
Credential-based compromises still need to be top of mind, but exploits on vulnerabilities are going to be the next target for frustrated attackers. They don’t need your password or MFA if they can sneak in the back door.
Mandiant’s 2023 Trends Report showed that Exploits (32%) surpassed Credential (14%) and Phishing (22%) as an initial vector of attack:
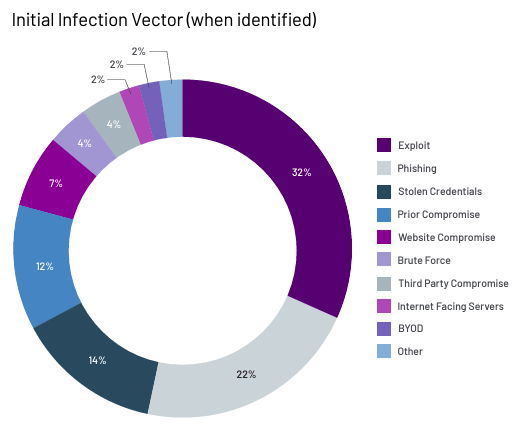
This is a little skewed from what Verizon reported in a much more expanded analysis that included a larger sample size in their 2023 Data Breach Investigations Report.
I included the attack vectors data since this is interesting to see side-by-side:

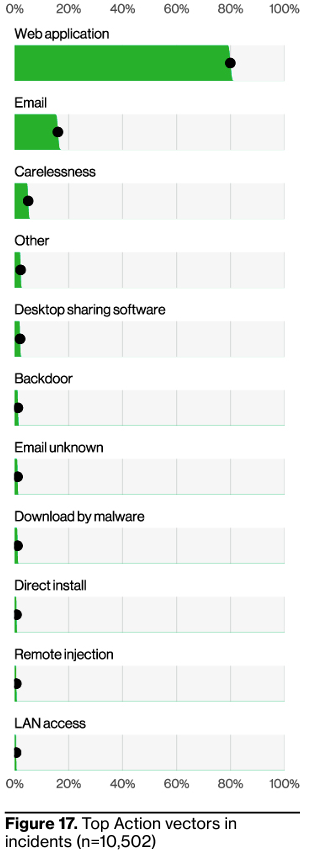
Verizon 2023 Data Breach Investigation Report (https://www.verizon.com/business/resources/reports/2023-data-breach-investigations-report-dbir.pdf)
However, when you look at attacks that involved virtual currency (a small sample of Verizon’s analysis), you see numbers much more like what Mandiant reported. Again, the vectors are included for added context:
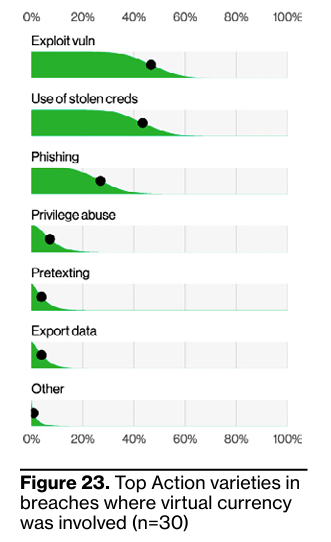

Verizon 2023 Data Breach Investigation Report (https://www.verizon.com/business/resources/reports/2023-data-breach-investigations-report-dbir.pdf)
I suspect that there’s a bit of an overlap in stats between Stolen Credential and Phishing attacks depending on who is doing the reporting or even the initial breach investigations. Phishing will often lead to a credential compromise, and if you combine these to 36% of the attacks investigated – it starts to tip beyond Exploits.
Either way, as MFA becomes more of a standard, it’s going to cause attackers to adjust their approach.
Time out!
We need a quick reality check. As I’m writing this, I realize we’re getting deep into some specific scenarios, and I don’t want to lead anyone astray.
It’s good to talk about and study attack vectors, but don’t get hung up here. You can get in a lot of trouble chasing trends. Chase ways to reduce all of your risks instead.
Focus on wholistic cybersecurity practices that continue to harden each year. Stay ahead of vulnerabilities and risks in general by having a good program.
Follow a framework like NIST or CIS. This isn’t a place to try to reinvent the wheel.
Identify > Detect > Protect > Respond > Recover
Then start over again.
Okay, now back to it!
Legislation will continue to evolve
2024 will bring some interesting changes to laws. New York has been leading the charge here ever since 23 NY DFS CRR 500 was introduced in 2017 and just recently was revised.
Over the last few years, we’ve seen more and more states adopt similar regulations that specifically affect Insurance and Financial Services. These all create trickle-down effects as they tend to include requirements around how to handle risks tied to 3rd party relationships.
Many of these laws are also in need of revisions. Cybersecurity is not a one-size-fits-all practice, so these laws need to be more structured to align with Risk-based Cybersecurity practices and they don’t really do the best job of that today. Many of them are only enforcing the bare-minimum best practices instead of creating the culture and practices that the frameworks I mentioned above are focused on.
Laws will be enforced
We’re also starting to see some of these laws start to be enforced and it’ll be interesting to watch the violations and penalties that come along with this.
New York just recently settled with a $1 million penalty to First American Title Insurance Company.
This was an early case for a very early cybersecurity law. This is one to read about for several reasons:
- This is setting a standard for other lawsuits to follow
- The fine is significant
- The violations cited against First American go beyond just meeting requirements – “quality” became important
- How you handle delegating your cybersecurity efforts also matters. It’s stated in the law itself: if you delegate, leaders are still responsible to ensure they get regular status reports and updates. And, company leaders need to be involved in ensuring what was delegated was done properly.
Cyber Liability will continue to evolve
In 2022 and 2023, Cyber Liability insurers have had to tighten up the way they assess risk and what goes into an application. It was necessary to avoid needlessly paying out claims when businesses were doing little to protect themselves.
Today, you can’t really get a policy if you didn’t have MFA in place on critical systems or if you don’t have certain practices like Backup and Recovery in place (just to name a couple of the minimum practices that are now expected).
While there’s still a lot of work to do here, I think there’s a ton of opportunity and am a huge supporter of Cyber Liability Insurance. I see more and more agencies making smart bets on growing this side of their book of business this year.
In 2024, I also expect to see more evolution in how applications and underwriting work. By this I mean more questions and increased minimum requirements.
I’ve seen more and more “security score” type of assessments come into the underwriting practice. It’s better, but those aren’t as informative as doing a real Cybersecurity Risk Assessment.
The catch here is that a true Risk Assessment takes time, energy, and money – enough to bump it out of a logistical underwriting practice for smaller businesses. However, until we find a way to get closer to doing a real in-depth assessment, we’ll continue to underestimate our risks.
Maybe someone will crack that in 2024. We do have some powerful AI tools on the horizon…
AI will be a big deal offensively and defensively
You didn’t think you’d get out of a 2024 predictions post without AI coming up, did you? I’m not going to beat this topic to death, but it does deserve a seat at the table here.
I know people have heard that attackers can now write better phishing emails – but that’s just scratching the surface.
Side note: We’re going to need to tighten our training on these things but also look at our defenses. Employees are a weak link in your security, so training them was always in the spirit of turning them into a human firewall. While that’s a good idea, I say you should try to remove them from the equation as much as possible. This goes back to having layers of security and defense-in-depth approaches.
AI can be used to not only write phishing attacks, but create new code and viruses. It can help do research quickly and put together an attack. All of these work efficiency hacks are available to attackers now too – and attackers are known to be extremely innovative and creative.
The good news is that AI has been used in cybersecurity for quite a while now. It’s a major component of NextGen Antivirus and other tools you probably already use in your office. In the past, I sold AI-based email security tools that would help identify phishing emails and remove them. These things have all been around before Chat GPT.
While attacks will advance, there’s already a lot of innovation coming on the defensive side of things that we’ll see come into the marketplace in 2024. Keep a close eye out for ways to leverage AI to protect yourself (just assess the risks of these tools before you implement them – this is a whole other topic I’ll cover in the future, but attackers have a knack for turning tools against ourselves).
I’ll leave it at that for the AI topic today, but this will be something that we come back to occasionally this year.
Conclusion
The nice thing about all of this is that 2024 isn’t written yet. We still can shape the future of what we do on the Cyber front.
Here’s some advice:
- Stop thinking of Cybersecurity as a sprint, or even as a marathon for that matter. It’s never done and will always be necessary as long as you have a computer or data.
- Get the minimum best practices handled immediately – but know that this is just the beginning, prepare to go beyond.
-
If you think you have it handled, you don’t. At that point, you need to ask what your new risks are, find them, and adjust.
Remember: Identify > Detect > Protect > Respond > Recover > REPEAT - Find a framework or 3rd party to help you figure out a path and a plan (message me and I’ll help point you in the right direction)
- Don’t keep Cybersecurity in just IT, it goes way beyond that and needs to be a part of the company culture and regular dialog.
- Get a strong Cyber Liability Policy and know what is expected of you to satisfy both your policy requirements and various legal requirements.
And, follow along with me this year to continue learning more. Join my newsletter below or follow me on LinkedIn.
Share

Ryan Smith
Ryan's experience across cybersecurity, sales, insurance, technology, education, and mathematics have helped him become a business-oriented problem solver that can simplify complex topics.
His eclectic and diverse background is now able to be leveraged by businesses that are interested in outside perspectives to help them overcome challenges.
Popular Posts

RLS Consulting Is (Re)Opening for Business!

Cybersecurity Begins at the Individual
The Buyer’s Challenge
Newsletter
Looking for Identity Theft Protection?
RLS Consulting is a proud distributor of defend-id ©.
Learn how protecting your employees from the perils of Identity Theft and Fraud can help your business security and overhead costs.
Want to sell defend-id through your insurance agency?
Learn More


